Fantasy – a new Agrius wiper deployed through a supply‑chain attack
- ESET Expert

- Dec 9, 2022
- 4 min read

ESET researchers analyzed a supply-chain attack abusing an Israeli software developer to deploy Fantasy, Agrius’s new wiper, with victims including the diamond industry.
ESET researchers discovered a new wiper and its execution tool, both attributed to the Agrius APT group, while analyzing a supply-chain attack abusing an Israeli software developer. The group is known for its destructive operations.
In February 2022, Agrius began targeting Israeli HR and IT consulting firms, and users of an Israeli software suite used in the diamond industry. We believe that Agrius operators conducted a supply-chain attack abusing the Israeli software developer to deploy their new wiper, Fantasy, and a new lateral movement and Fantasy execution tool, Sandals.
The Fantasy wiper is built on the foundations of the previously reported Apostle wiper but does not attempt to masquerade as ransomware, as Apostle originally did. Instead, it goes right to work wiping data. Victims were observed in South Africa – where reconnaissance began several weeks before Fantasy was deployed – Israel, and Hong Kong.
Key points of this blogpost:
Agrius conducted a supply-chain attack abusing an Israeli software suite used in the diamond industry.
The group then deployed a new wiper we named Fantasy. Most of its code base comes from Apostle, Agrius’s previous wiper.
Along with Fantasy, Agrius also deployed a new lateral movement and Fantasy execution tool that we have named Sandals.
Victims include Israeli HR firms, IT consulting companies, and a diamond wholesaler; a South African organization working in the diamond industry; and a jeweler in Hong Kong.
Group overview
Agrius is a newer Iran-aligned group targeting victims in Israel and the United Arab Emirates since 2020. The group initially deployed a wiper, Apostle, disguised as ransomware, but later modified Apostle into fully fledged ransomware. Agrius exploits known vulnerabilities in internet-facing applications to install webshells, then conducts internal reconnaissance before moving laterally and then deploying its malicious payloads.
Campaign overview
On February 20th, 2022 at an organization in the diamond industry in South Africa, Agrius deployed credential harvesting tools, probably in preparation for this campaign. Then, on March 12th, 2022, Agrius launched the wiping attack by deploying Fantasy and Sandals, first to the victim in South Africa and then to victims in Israel and lastly to a victim in Hong Kong.
Victims in Israel include an IT support services company, a diamond wholesaler, and an HR consulting firm. South African victims are from a single organization in the diamond industry, with the Hong Kong victim being a jeweler.
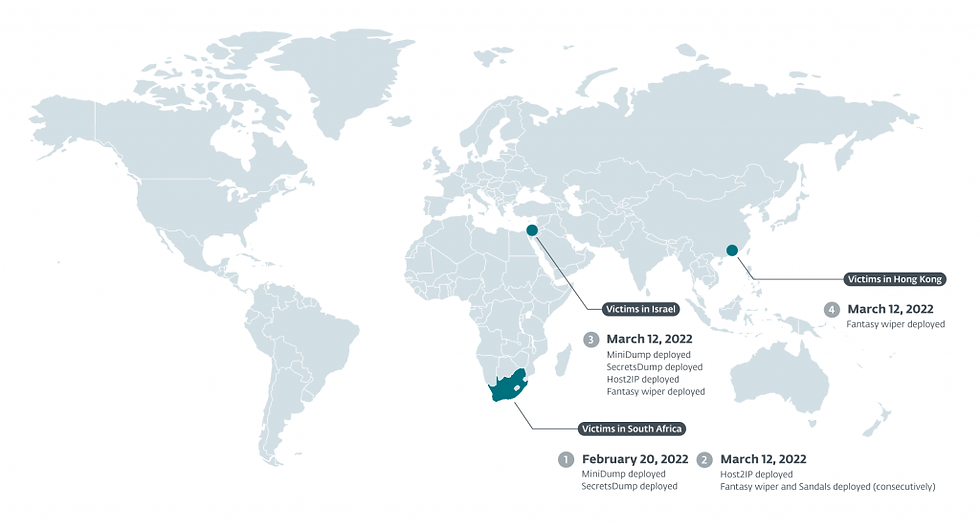
Figure 1. Victim timeline and locations
The campaign lasted less than three hours and within that timeframe ESET customers were already protected with detections identifying Fantasy as a wiper, and blocking its execution. We observed the software developer pushing out clean updates within a matter of hours of the attack. We reached out to the software developer to notify them about a potential compromise, but our enquiries went unanswered.
Preparing for departure
The first tools deployed by Agrius operators to victim systems, through means unknown, were:
MiniDump, “a C# implementation of mimikatz/pypykatz minidump functionality to get credentials from LSASS dumps”
SecretsDump, a Python script that “performs various techniques to dump hashes from [a] remote machine without executing any agent there”
Host2IP, a custom C#/.NET tool that resolves a hostname to an IP address.
Usernames, passwords, and hostnames collected by these tools are required for Sandals to successfully spread and execute the Fantasy wiper. Agrius operators deployed MiniDump and SecretsDump to this campaign’s first victim on February 20th, 2022, but waited until March 12th, 2022 to deploy Host2IP, Fantasy, and Sandals (consecutively).
Sandals: Igniting the Fantasy (wiper)
Sandals is a 32-bit Windows executable written in C#/.NET. We chose the name because Sandals is an anagram of some of the command line arguments it accepts. It is used to connect to systems in the same network via SMB, to write a batch file to disk that executes the Fantasy wiper, and then run that batch file via PsExec with this command line string:
PsExec.exe /accepteula -d -u “<username>” -p “<password>” -s “C:\<path>\<GUID>.bat”
The PsExec options have the following meanings:
-d – Don’t wait for process to terminate (non-interactive).
/accepteula – Suppress display of the license dialog.
-s – Run the remote process in the SYSTEM account.
Sandals does not write the Fantasy wiper to remote systems. We believe that the Fantasy wiper is deployed via a supply-chain attack using the software developer’s software update mechanism. This assessment is based on several factors:
all victims were customers of the affected software developer;
the Fantasy wiper was named in a similar fashion to legitimate versions of the software;
all victims executed the Fantasy wiper within a 2.5 hour timeframe, where victims in South Africa were targeted first, then victims in Israel, and finally victims in Hong Kong (we attribute the delay in targeting to time zone differences and a hardcoded check-in time within the legitimate software); and,
lastly, the Fantasy wiper was written to, and executed from, %SYSTEM%\Windows\Temp, the default temp directory for Windows systems.
Additionally, we believe the victims were already using PsExec, and Agrius operators chose to use PsExec to blend into typical administrative activity on the victims’ machines, and for ease of batch file execution.
Conclusion
Since its discovery in 2021, Agrius has been solely focused on destructive operations. To that end, Agrius operators probably executed a supply-chain attack by targeting an Israeli software company’s software updating mechanisms to deploy Fantasy, its newest wiper, to victims in Israel, Hong Kong, and South Africa. Fantasy is similar in many respects to the previous Agrius wiper, Apostle, that initially masqueraded as ransomware before being rewritten to be actual ransomware. Fantasy makes no effort to disguise itself as ransomware. Agrius operators used a new tool, Sandals, to connect remotely to systems and execute Fantasy.
For more information, read here - https://www.welivesecurity.com/2022/12/07/fantasy-new-agrius-wiper-supply-chain-attack/



Comments